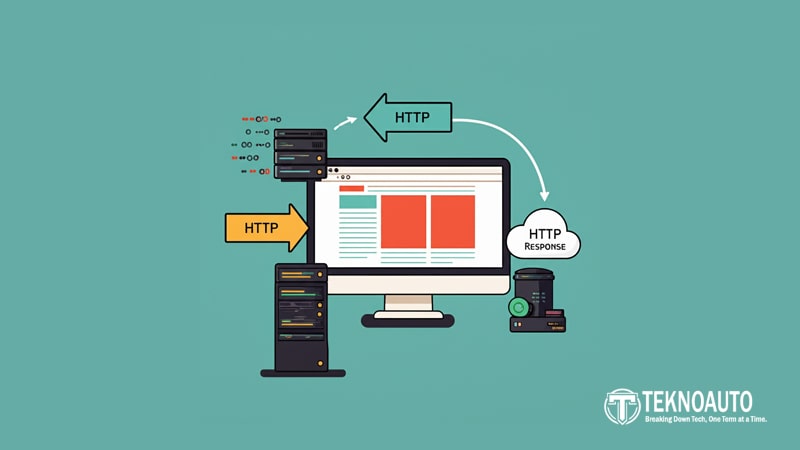
The internet, as we know it, thrives on a silent, yet powerful workhorse: the Hypertext Transfer Protocol, or HTTP. Every time you type a web address, click a link, or stream a video, you’re engaging with HTTP.
But what exactly is it? This exploration delves into the intricate workings of Exploring HTTP: The Protocol Behind Every Web Page, revealing its fundamental role in facilitating communication between your web browser and the servers that host the content you crave.
From its humble beginnings to its modern iterations, understanding HTTP is key to comprehending the very fabric of the web.
The Foundation of the Web: A History of HTTP
Before diving into the technical details, let’s take a brief journey through the history of HTTP. Its evolution mirrors the evolution of the World Wide Web itself.
- HTTP/0.9 (1991): The rudimentary beginning. This version was incredibly simple, allowing only GET requests to retrieve HTML documents. There were no headers, no status codes, and no support for anything beyond basic text.
- HTTP/1.0 (1996): The first officially specified version, HTTP/1.0 introduced headers, allowing for metadata to be sent along with the request and response. Status codes were also introduced, providing feedback on the success or failure of the request. This version allowed for the transfer of different types of documents, not just HTML.
- HTTP/1.1 (1999): A significant improvement over HTTP/1.0. HTTP/1.1 introduced persistent connections, allowing multiple requests to be sent over the same TCP connection, reducing latency. It also added support for features like pipelining, chunked transfer encoding, and host headers, enabling virtual hosting (multiple websites on the same IP address). HTTP/1.1 remains widely used today.
- HTTP/2 (2015): Designed to address the performance limitations of HTTP/1.1, HTTP/2 introduces features like multiplexing (multiple requests and responses over a single TCP connection), header compression (using HPACK), and server push (the server proactively sends resources to the client). This version significantly improves page load times, especially on connections with high latency.
- HTTP/3 (2020): The newest iteration, HTTP/3, moves away from TCP and adopts UDP as its transport protocol, using QUIC (Quick UDP Internet Connections). QUIC offers improved performance, especially in lossy network conditions, and provides better security with built-in encryption. HTTP/3 is still being widely adopted, but promises to further enhance the web experience.
This historical context is crucial for understanding the design choices and the improvements made in each version of HTTP. Each iteration has aimed to improve speed, efficiency, and security, reflecting the ever-increasing demands of the modern web.
HTTP: A Request-Response Protocol
At its core, HTTP is a request-response protocol. This means that a client (typically a web browser) sends a request to a server, and the server processes that request and sends back a response. This interaction is the fundamental building block of every web interaction. Let’s break down the components of a request and a response.
The HTTP Request
An HTTP request is composed of several key elements:
1. Method (or Verb): Indicates the action the client wants to perform on the resource. Common methods include:
- GET: Retrieves a resource. This is the most common method, used for fetching web pages, images, and other content.
- POST: Sends data to the server to create or update a resource. Used for submitting forms, uploading files, etc.
- PUT: Replaces an existing resource with the data provided in the request.
- DELETE: Deletes a specified resource.
- PATCH: Applies partial modifications to a resource.
- HEAD: Similar to GET, but only retrieves the headers, not the body of the response. Useful for checking if a resource has been modified.
- OPTIONS: Requests information about the communication options available for a resource.
- CONNECT: Establishes a tunnel to the server identified by the target resource. Commonly used for SSL tunneling.
- TRACE: Performs a message loop-back test along the path to the target resource.
Here’s a table summarizing the HTTP methods:
| Method | Description |
|---|---|
| GET | Retrieves a resource. |
| POST | Sends data to the server to create or update a resource. |
| PUT | Replaces an existing resource with the data provided in the request. |
| DELETE | Deletes a specified resource. |
| PATCH | Applies partial modifications to a resource. |
| HEAD | Retrieves only the headers of a resource. |
| OPTIONS | Requests information about the communication options for a resource. |
| CONNECT | Establishes a tunnel to the server identified by the target resource. |
| TRACE | Performs a message loop-back test along the path to the target resource. |
2. URI (Uniform Resource Identifier): Identifies the resource the client wants to access. This is often a URL (Uniform Resource Locator), which specifies the location of the resource on the web. For example, https://www.example.com/index.html.
3. HTTP Version: Specifies the version of the HTTP protocol being used (e.g., HTTP/1.1, HTTP/2).
4. Headers: Provide additional information about the request, such as:
Host: Specifies the hostname of the server.User-Agent: Identifies the client software (e.g., browser).Accept: Specifies the content types the client can handle.Accept-Language: Specifies the preferred languages for the response.Cookie: Sends cookies to the server.Authorization: Provides authentication credentials.
Here’s an example of a simple HTTP request:
<br />GET /index.html HTTP/1.1<br />Host: www.example.com<br />User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.124 Safari/537.36<br />Accept: text/html,application/xhtml+xml,application/xml;q=0.9,<em>/</em>;q=0.8<br />Accept-Language: en-US,en;q=0.5<br />
5. Body (Optional): Contains data being sent to the server, often used with POST, PUT, and PATCH requests. For example, form data or JSON payloads.
The HTTP Response
The server responds to the client’s request with an HTTP response, which also consists of several key elements:
1. Status Code: A three-digit code that indicates the outcome of the request. Common status codes include:
200 OK: The request was successful.
301 Moved Permanently: The resource has been moved to a new location.
400 Bad Request: The request was malformed and could not be understood.
404 Not Found: The requested resource was not found on the server.
500 Internal Server Error: An error occurred on the server.
Here’s a table summarizing common HTTP status codes:
| Status Code | Description |
|---|---|
| 200 OK | The request was successful. |
| 301 Moved Permanently | The resource has been moved to a new location. |
| 400 Bad Request | The request was malformed and could not be understood. |
| 404 Not Found | The requested resource was not found on the server. |
| 500 Internal Server Error | An error occurred on the server. |
2. Reason Phrase: A human-readable explanation of the status code (e.g., “OK” for 200, “Not Found” for 404).
3. HTTP Version: Specifies the version of the HTTP protocol being used (e.g., HTTP/1.1, HTTP/2).
4. Headers: Provide additional information about the response, such as:
Content-Type: Specifies the content type of the response body (e.g., text/html, application/json).Content-Length: Specifies the size of the response body in bytes.Set-Cookie: Sets a cookie in the client’s browser.Cache-Control: Specifies caching policies for the resource.
Here’s an example of a simple HTTP response:
``<br />HTTP/1.1 200 OK<br />Content-Type: text/html; charset=UTF-8<br />Content-Length: 1234</p><p><br /></p><p style="text-align: left;"><span style="font-size: x-large;">Hello, World!</span></p><p><br /></p><p>5. <strong>Body:</strong> Contains the actual data being returned to the client. This could be HTML, JSON, images, or any other type of content.</p><p>Understanding the structure of HTTP requests and responses is crucial for debugging web applications and optimizing performance.</p><h2 style="text-align: left;">HTTP Methods in Detail</h2><p>Let's delve deeper into some of the most commonly used HTTP methods:</p><h3 style="text-align: left;">GET: Retrieving Resources</h3><p>The GET method is the workhorse of the web. It's used to retrieve resources from the server. When you type a URL into your browser and press enter, your browser sends a GET request to the server. The server then responds with the requested resource, which could be an HTML page, an image, or any other type of content.</p><p>GET requests should be <em>idempotent</em>, meaning that making the same GET request multiple times should have the same effect as making it once. They should also be <em>safe</em>, meaning that they should not have any side effects on the server.</p><h3 style="text-align: left;">POST: Sending Data to the Server</h3><p>The POST method is used to send data to the server to create or update a resource. This is commonly used for submitting forms, uploading files, and sending API requests.</p><p>Unlike GET requests, POST requests are not idempotent. Making the same POST request multiple times could have different effects on the server, such as creating multiple entries in a database.</p><h3 style="text-align: left;">PUT: Replacing Resources</h3><p>The PUT method is used to replace an existing resource with the data provided in the request. This method is often used for updating entire resources.</p><p>PUT requests are idempotent. Making the same PUT request multiple times should have the same effect as making it once (i.e., the resource will be replaced with the same data).</p><h3 style="text-align: left;">DELETE: Deleting Resources</h3><p>The DELETE method is used to delete a specified resource. This method is often used for removing data from a server.</p><p>DELETE requests are also idempotent. Making the same DELETE request multiple times should have the same effect as making it once (i.e., the resource will be deleted).</p><h3 style="text-align: left;">PATCH: Applying Partial Modifications</h3><p>The PATCH method is used to apply partial modifications to a resource. This is useful when you only need to update a small part of a resource, rather than replacing the entire thing.</p><p>PATCH requests are not necessarily idempotent. Whether a PATCH request is idempotent depends on the specific implementation.</p><h2 style="text-align: left;">HTTP Headers: Metadata and Control</h2><p>HTTP headers play a crucial role in providing additional information about requests and responses, allowing for fine-grained control over the communication between client and server.</p><h3 style="text-align: left;">Request Headers</h3><p>Request headers provide information about the client and the type of content it can handle. Some common request headers include:</p><ul> <li><strong>Host:</strong> Specifies the hostname of the server. This is essential for virtual hosting, where multiple websites share the same IP address.</li> </ul><ul> <li><strong>User-Agent:</strong> Identifies the client software (e.g., browser, mobile app). This allows the server to tailor the response to the specific client.</li> </ul><ul> <li><strong>Accept:</strong> Specifies the content types the client can handle. This allows the server to send the most appropriate content type for the client.</li> </ul><ul> <li><strong>Accept-Language:</strong> Specifies the preferred languages for the response. This allows the server to send content in the user's preferred language.</li> </ul><ul> <li><strong>Cookie:</strong> Sends cookies to the server. Cookies are small pieces of data that the server can store on the client's machine and retrieve later.</li> </ul><ul> <li><strong>Authorization:</strong> Provides authentication credentials. This is used for accessing protected resources.</li> </ul><ul> <li><strong>Cache-Control:</strong> Specifies caching policies for the request. This allows the client to control how the response is cached.</li> </ul><h3 style="text-align: left;">Response Headers</h3><p>Response headers provide information about the server and the content being returned. Some common response headers include:</p><ul> <li><strong>Content-Type:</strong> Specifies the content type of the response body (e.g.,text/html,application/json). This tells the client how to interpret the response body.</li> </ul><ul> <li><strong>Content-Length:</strong> Specifies the size of the response body in bytes. This allows the client to know how much data to expect.</li> </ul><ul> <li><strong>Set-Cookie:</strong> Sets a cookie in the client's browser. This allows the server to store data on the client's machine.</li> </ul><ul> <li><strong>Cache-Control:</strong> Specifies caching policies for the response. This tells the client how the response should be cached.</li> </ul><ul> <li><strong>Location:</strong> Specifies the URL to which the client should be redirected. This is used for redirects (e.g., 301 Moved Permanently).</li> </ul><ul> <li><strong>Server:</strong> Identifies the server software. This can be useful for debugging purposes.</li> </ul><p>Understanding HTTP headers is essential for optimizing web performance, implementing caching strategies, and securing web applications.</p><h2 style="text-align: left;">HTTP and Security: HTTPS</h2><p>Security is paramount on the modern web. HTTP, in its original form, transmits data in plain text, making it vulnerable to eavesdropping and tampering. This is where HTTPS (HTTP Secure) comes in.</p><p>HTTPS is not a separate protocol, but rather HTTP over TLS/SSL (Transport Layer Security/Secure Sockets Layer). TLS/SSL encrypts the communication between the client and the server, preventing third parties from intercepting and reading the data.</p><p>When you see "https://" in the address bar, it means that the connection is encrypted using TLS/SSL. The server provides a digital certificate, which verifies its identity and allows the client to establish a secure connection.</p><p>HTTPS is essential for protecting sensitive data, such as passwords, credit card numbers, and personal information. It also helps to prevent man-in-the-middle attacks, where an attacker intercepts the communication between the client and the server.</p><h2 style="text-align: left;">The Importance of Status Codes</h2><p>HTTP status codes are crucial for understanding the outcome of a request. They provide a standardized way for the server to communicate the status of the request to the client. Status codes are grouped into five classes:</p><ul> <li><strong>1xx (Informational):</strong> The request was received and is being processed.</li> </ul><ul> <li><strong>2xx (Success):</strong> The request was successfully received, understood, and accepted.</li> </ul><ul> <li><strong>3xx (Redirection):</strong> Further action needs to be taken by the client to complete the request.</li> </ul><ul> <li><strong>4xx (Client Error):</strong> The request contains bad syntax or cannot be fulfilled.</li> </ul><ul> <li><strong>5xx (Server Error):</strong> The server failed to fulfill an apparently valid request.</li> </ul><p>Understanding these categories, and the specific status codes within them, is essential for debugging web applications and handling errors gracefully. For example:</p><ul> <li><strong>200 OK:</strong> Indicates that the request was successful and the server is returning the requested resource.</li> </ul><ul> <li><strong>301 Moved Permanently:</strong> Indicates that the resource has been moved to a new location, and the client should update its bookmarks.</li> </ul><ul> <li><strong>400 Bad Request:</strong> Indicates that the client sent a malformed request, which the server could not understand.</li> </ul><ul> <li><strong>401 Unauthorized:</strong> Indicates that the client needs to authenticate before accessing the resource.</li> </ul><ul> <li><strong>403 Forbidden:</strong> Indicates that the client does not have permission to access the resource.</li> </ul><ul> <li><strong>404 Not Found:</strong> Indicates that the requested resource could not be found on the server.</li> </ul><ul> <li><strong>500 Internal Server Error:</strong> Indicates that an error occurred on the server, and the request could not be fulfilled.</li> </ul><ul> <li><strong>503 Service Unavailable:</strong> Indicates that the server is temporarily unavailable, usually due to maintenance or overload.</li> </ul><p>By properly interpreting status codes, developers can build more robust and user-friendly web applications.</p><h2 style="text-align: left;">HTTP Caching: Optimizing Performance</h2><p>Caching is a crucial technique for improving the performance of web applications. By storing frequently accessed resources in a cache, you can reduce the number of requests that need to be sent to the server, resulting in faster page load times.</p><p>HTTP provides several mechanisms for caching resources:</p><ul> <li><strong>Browser Cache:</strong> The browser can cache resources locally on the user's machine. This is the fastest type of caching, as the resource is retrieved directly from the browser's cache without contacting the server.</li> </ul><ul> <li><strong>Proxy Cache:</strong> A proxy server can cache resources on behalf of multiple clients. This can reduce the load on the server and improve performance for users who are geographically close to the proxy server.</li> </ul><ul> <li><strong>Server Cache:</strong> The server itself can cache resources in memory or on disk. This can reduce the load on the database and improve response times.</li> </ul><p>HTTP headers, such asCache-Control,Expires, andETag, are used to control how resources are cached.</p><ul> <li><strong>Cache-Control:</strong> This header allows the server to specify caching policies for the resource. For example,Cache-Control: max-age=3600tells the client to cache the resource for 3600 seconds (1 hour). Common directives includepublic,private,no-cache, andno-store.</li> </ul><ul> <li><strong>Expires:</strong> This header specifies the date and time after which the resource should be considered stale.</li> </ul><ul> <li><strong>ETag:</strong> This header provides a unique identifier for the resource. The client can send theETag¨C29C304 Not Modified¨C30Ccurl¨C31Ccurl` is a powerful tool for testing APIs and debugging HTTP traffic.
- Wireshark: A network protocol analyzer that allows you to capture and analyze network traffic, including HTTP traffic.
- Fiddler: A free web debugging proxy that allows you to inspect HTTP and HTTPS traffic between your computer and the internet.
By using these tools and techniques, you can gain valuable insights into how your web applications are communicating over HTTP and identify potential problems.
Best Practices for HTTP
To ensure optimal performance, security, and reliability, it’s important to follow best practices for HTTP:
- Use HTTPS: Always use HTTPS to encrypt communication between the client and the server.
- Optimize Caching: Properly configure HTTP caching to reduce the number of requests that need to be sent to the server.
- Minimize Request Size: Reduce the size of HTTP requests by compressing data, minimizing the number of headers, and using efficient data formats like JSON.
- Use a CDN (Content Delivery Network): Use a CDN to distribute your content to servers around the world, improving performance for users who are geographically distant from your origin server.
- Keep Connections Alive: Use persistent connections (HTTP Keep-Alive) to reduce the overhead of establishing new connections for each request.
- Use HTTP/2 or HTTP/3: Consider upgrading to HTTP/2 or HTTP/3 to take advantage of their performance benefits.
- Handle Errors Gracefully: Implement proper error handling to provide informative error messages to users.
- Validate Input: Always validate user input to prevent security vulnerabilities like cross-site scripting (XSS) and SQL injection.
By following these best practices, you can build more efficient, secure, and reliable web applications.
The Future of HTTP
HTTP continues to evolve to meet the ever-changing demands of the web. HTTP/3 is gaining traction, and new features and extensions are being developed all the time.
Some potential future directions for HTTP include:
- Further improvements in performance: Research and development will continue to focus on improving the speed and efficiency of HTTP.
- Enhanced security: New security features will be added to protect against emerging threats.
- Better support for real-time applications: HTTP will be adapted to better support real-time applications like streaming video and online gaming.
- Integration with new technologies: HTTP will be integrated with new technologies like WebAssembly and serverless computing.
The future of HTTP is bright, and the protocol will continue to play a vital role in the evolution of the web.
Conclusion: The Indispensable Protocol
Exploring HTTP: The Protocol Behind Every Web Page reveals a system far more complex and sophisticated than a simple request and response. It’s a constantly evolving technology, adapting to the ever-increasing demands of the modern web. From its humble beginnings to its cutting-edge iterations, HTTP remains the fundamental language of the internet, enabling us to access and interact with the vast world of online information and services.
Understanding HTTP, therefore, is essential for anyone involved in web development, network administration, or simply wanting a deeper appreciation of how the internet works. As the web continues to evolve, so too will HTTP, ensuring its continued relevance as the cornerstone of online communication.